Vault-level security
IDEX delivers biometric authentication built to withstand AI-driven attacks
Discover vault-level security
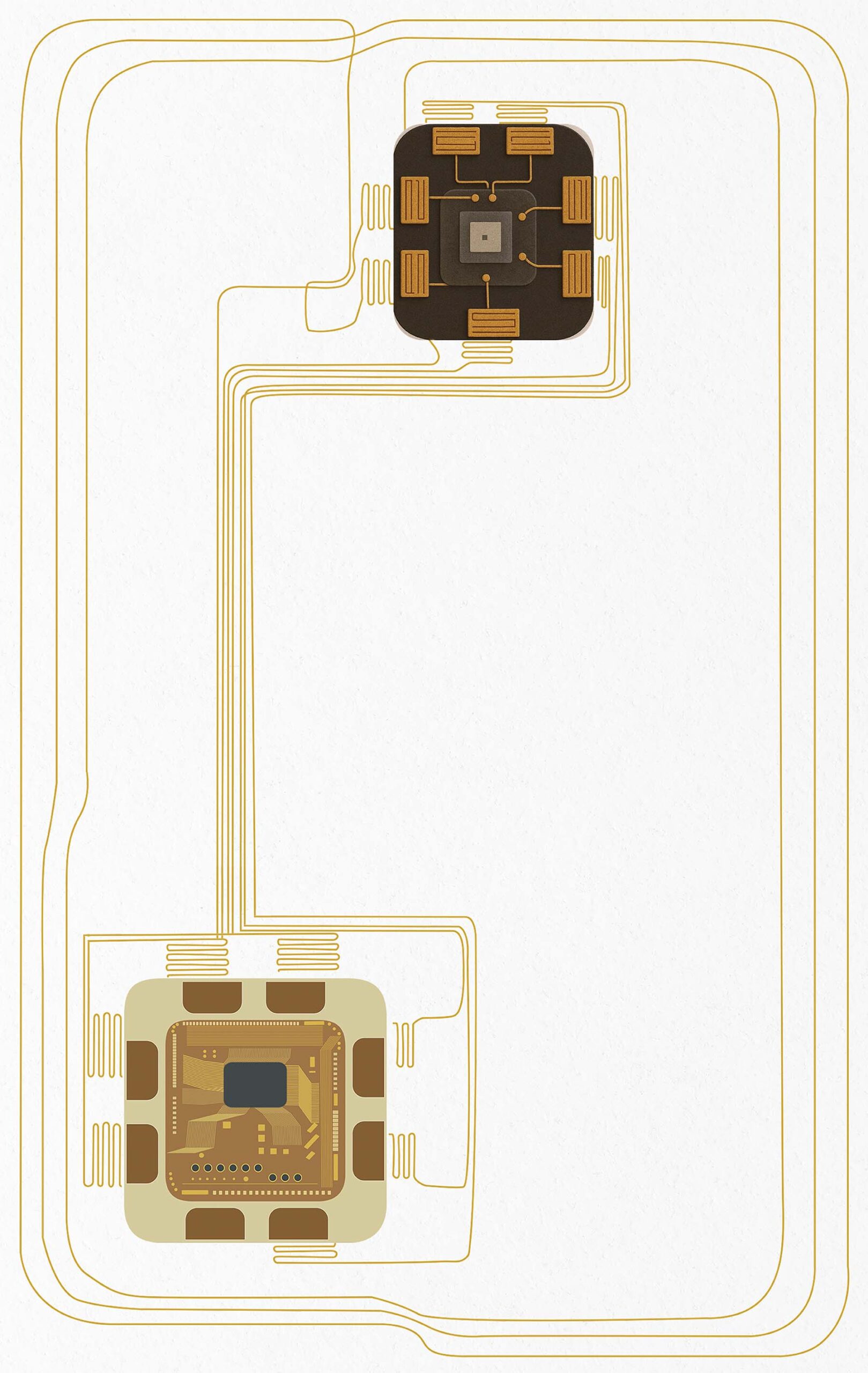
Secure element
The secure element protects access keys and biometric data, performing authentication securely on the card so sensitive data never leaves the device.
- Protects keys and biometric templates
- Executes authentication securely on-card
- EAL6+ certified
Fingerprint sensor
Our capacitive fingerprint sensor enables fast, accurate biometric verification in a card form factor for access and payment scenarios.
- Integrated advanced spoof protection
- Lightning-fast 250ms fingerprint verification
- Certified by Visa and Mastercard
Strong biometric protection
Artificial spoof detection
The sensor can distinguish between genuine, living skin and artificial replicas such as gelatine, silicone, rubber or printed images. It analyses skin structure, moisture and other biometric vital signs.
Finger liveness detection
Advanced algorithms verify that the fingerprint comes from a living person at the moment the transaction is conducted. This prevents the use of stolen fingerprint images or artificial replicas.
Your fingerprint stays with you
Privacy is central to our design; therefore, fingerprint data never leaves the card and is never stored as an image.
Fingerprint not stored in cloud
Biometric data is stored on the card, with fingerprint verification performed locally and never shared with anyone.
Fingerprint not stored as image
Your fingerprint is converted into an encrypted template that cannot be reconstructed outside the card.
GDPR
compliant
Biometric data stays on the card, not in central systems or the cloud – supporting GDPR privacy by design.
When security and auditing are critical
With IDEX Biometric Card, access is bound to the cardholder’s fingerprint. Every access is trackable, enabling precise auditing and eliminating misuse from shared, borrowed, or lost cards.
In selected high-security zones, access can be restricted to biometric authentication only.
Phishing-proof authentication
Our card uses FIDO2 protocol for digital authentication. It’s designed from the ground up to stop phishing and Adversary-in-the-Middle attacks.
Your private access key never leaves the card
Your private key is generated and stored securely on the card and never leaves it. Only a one-time cryptographic signature is shared.
Access keys are locked to specific websites
Each key is bound to a specific domain – a key for yourbank.com won’t work on yourbank-login.com.
Every login is unique
Each login uses a unique challenge that is signed by the card, making intercepted data useless for future logins.






Fingerprint sensor performance
Our fingerprint sensor is designed for fast and accurate fingerprint verification, with low error rates and minimal user friction.
250 ms
Biometric verification time
<1.5%
False rejection rate
<1:20 000
False acceptance rate
9.5 mm
9.5×9.5 mm large sensing area
2 fingers
Support for registering multiple fingers
6 touches
Enrolment only required 6 touches*
* Biometric matching is improved during initial use through secure, on-card template refinement.
Want to explore the technical details?
Download the product sheet for detailed specifications and technical information.
Download product sheetSecurity FAQ
Common questions on security and certification
No. Fingerprint data is never uploaded or stored in the cloud. It remains securely stored inside the card. The fingerprint is converted into an encrypted mathematical template that cannot be reconstructed or reused elsewhere. This removes the need for central biometric databases and supports strict privacy and GDPR requirements.
Biometric authentication cannot be used by anyone other than the authorised cardholder. A lost or stolen card therefore cannot be used to authenticate biometrically.
In addition, the card can be revoked through the access or identity systems controlled by the organisation. Once revoked, the card is prevented from being used and can be replaced following standard procedures.
No. The card works only with the enrolled fingerprint. Even if another person has physical possession of the card, access will be denied.
This prevents card sharing and misuse, and ensures that access is always tied to a verified individual.
No. When the card is not close to a compatible reader, it is completely inactive and has no power. There is no active interface or connection that can be targeted remotely.
The card only becomes active for a brief moment when it is held near a reader, drawing power from the reader itself. When removed, it immediately returns to a passive state.
The card uses advanced liveness detection to verify genuine human touch. This prevents access using fake fingerprints, printed images, or artificial materials.
Liveness checks are performed directly on the card and cannot be bypassed by readers or terminals, providing strong protection against presentation attacks.
Data exchanged inside the card is protected through encrypted communication between the fingerprint sensor and the secure element on the card. This prevents internal data from being intercepted or altered.
Industry-standard encryption is used, including AES-128, providing an additional layer of protection even in advanced attack scenarios.
Passwords and one-time codes rely on shared secrets that can be stolen, intercepted, or reused.
Biometric, card-based authentication uses hardware-protected cryptographic keys that are only activated after successful biometric verification. This removes shared secrets and significantly reduces the risk of phishing and credential theft.
Biometric authentication verifies the individual locally on the card, while FIDO uses public-key cryptography to authenticate securely to systems and services.
The biometric check unlocks a cryptographic key stored on the card, which is then used for FIDO authentication. Because no shared secrets are transmitted or stored centrally, this approach provides strong protection against phishing and credential theft.
The card meets leading global security and payment standards, including Visa and Mastercard certification, FIDO2 certification, and compliance with EMVCo biometric requirements.
Its Secure Element is certified to EAL6+, ensuring a high level of protection for cryptographic keys.

